The cost of recovering from ransomware has surged to an average of $2.73 million per incident, excluding ransom payments. This is a stark reminder of the escalating risks facing the construction and real estate industries. As digital tools and technologies continue to revolutionize these fields, firms will need to contend with increasingly sophisticated cyberattacks that target project data, financial systems, and supply chains. A proactive approach to cybersecurity is no longer optional; it is truly critical for safeguarding operations, finances, and reputations.
A Growing Threat Landscape
Cybercriminals are exploiting vulnerabilities that are unique to construction and real estate firms, ranging from outdated systems to reliance on third-party vendors. The top threats include:
- Ransomware: Over the past year, nearly every attack in the construction and real estate sectors has also targeted
backups, with 61 percent of attempts successfully compromising these resources — slightly higher than the overall rate of 57 percent. - Phishing and Social Engineering: Responsible for over 50 percent of breaches, these attacks exploit human error through email and text-based schemes.
- Supply Chain Vulnerabilities: Weaknesses in vendor systems create entry points for attackers, leading to cascading consequences across projects.
AI-Driven Threats: Advanced technologies such as deepfake audio and video enable cybercriminals to manipulate financial transactions and erode trust.
Root Causes of Ransomware Attacks (2023-2024)
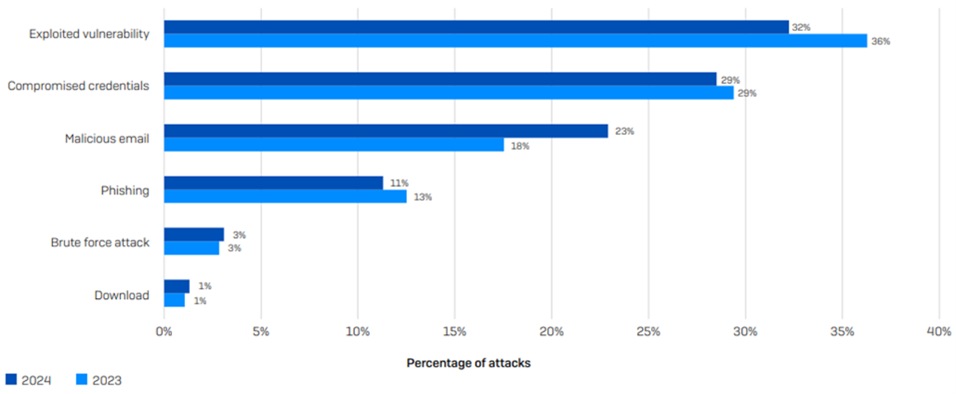
Source: The State of Ransomware 2024 by Sophos, April 2024
Ransomware
Ransomware attacks often bring operations to a standstill, forcing firms to choose between paying a ransom or enduring prolonged downtime. In 2024, only 28 percent of organizations were able to recover from ransomware within a week, a significant drop from prior years. Additionally, the time it takes to recover from a ransomware attack is steadily getting longer. The slowdown may indicate more complex attacks and/or lack of preparation.
Construction and real estate firms, which rely heavily on digital blueprints, project schedules, and client data, are particularly vulnerable. The ripple effects of an attack can include missed deadlines, budget overruns, and reputational damage. To mitigate these risks, firms will want to conduct regular risk assessments, implement advanced detection tools, and ensure that incident response plans are well-practiced.
Phishing and Social Engineering
Phishing and social engineering attacks exploit trust and human error, making them highly effective. Tactics include deceptive emails and fake text messages (smishing) that trick employees into revealing sensitive information or clicking malicious links. Nearly half of all breaches begin with compromised login credentials, which shows the need for robust authentication processes and user training.
Mitigation strategies include implementing multi-factor authentication across all systems, conducting regular phishing simulations, and offering ongoing training to keep cybersecurity practices top of mind. These proactive measures help foster a culture of awareness and vigilance.
Supply Chain Vulnerabilities
The interconnected reality of the construction and real estate industries makes supply chain vulnerabilities another critical risk. Vendors and subcontractors often handle sensitive project data, yet their cybersecurity practices may not meet required standards. Examples of vulnerabilities include outdated software, weak passwords, and insufficient encryption.
To reduce exposure, firms can conduct vendor risk assessments by requesting SOC 2 reports and evaluating compliance with frameworks like CMMC. Contracts can outline clear cybersecurity requirements, including regular audits. Continuous monitoring of vendor systems and secure integration into internal networks further strengthens defenses.
AI-Powered Cybercrime
Artificial intelligence is transforming cybercrime tactics. AI-powered phishing campaigns can mimic the writing styles of trusted contacts, which makes fraudulent emails more convincing than ever. Deepfake technology allows attackers to create realistic audio and video impersonations of executives or clients to manipulate financial transactions.
Organizations can address these threats by educating employees to recognize AI-generated content. Financial transactions, especially, should be verified through multiple trusted channels. Responsible use of AI tools to enhance security, aligned with frameworks like the NIST AI Risk Management Framework, helps mitigate these risks while maintaining ethical standards.
Cybersecurity Checklist: Key Actions for Resilience
A strong cybersecurity strategy calls for ongoing prevention, preparation, and improvement. Key areas include:
Proactive Measures
- Patch Management: Regularly update software and systems to eliminate vulnerabilities.
- Strong Password Practices: Implement multi-factor authentication (MFA) and use password managers for secure access.
- Employee Training: Provide regular training to help employees identify phishing attempts and social engineering tactics. Reinforce with ongoing training and phishing simulations.
Backup and Recovery Planning
- Frequent Backup Schedules: Align backups with your organization’s tolerance for data loss — hourly or daily backups are recommended.
- Test Backups: Regularly verify that backups are functional and can be restored in crisis.
- Collaborate with IT Providers: Work with managed service providers (MSPs) to optimize backup configurations and simulate recovery scenarios.
Email Security
- Email Protection Tools: Invest in robust email security tools and ensure they are properly configured. Misconfigurations can render expensive tools ineffective.
- Phishing Simulations: Regularly test employees with simulated phishing emails to reinforce awareness.
- Technical Safeguards: Enable filters to block malicious attachments and links before they reach inboxes.
Securing the Supply Chain
- Vendor Risk Assessments: Evaluate vendor cybersecurity practices through security questionnaires or third-party audits (e.g., SOC 2 reports).
- Cybersecurity Clauses: Incorporate clear security requirements into contracts, including obligations for data protection, compliance, and incident reporting.
- Ongoing Monitoring: Periodically reassess vendor security, particularly for high-risk partners.
Addressing AI Threats
- Deepfake Awareness: Train employees to verify audio or video requests by independently contacting the purported sender using known contact details.
- AI Risk Management: Leverage resources like the NIST AI Risk Management Framework to implement governance and controls for AI technologies.
- Enhanced Monitoring: Use AI-driven tools to detect anomalies and potential breaches.
Cyber Insurance
- Review Coverage: Evaluate cyber insurance policies to understand coverage limitations, including sub-limits for ransomware incidents.
- Ensure Compliance: Meet baseline security standards, such as MFA and regular risk assessments, to avoid denied claims.
- Tailor Policies: Work with insurers to develop coverage that aligns with industry-specific risks and operational needs.
Building resilience is more than reactive measures — it’s about a proactive, ongoing commitment to safeguarding project, client, and tenant data, as well as critical operations. The steps you take today to strengthen your defenses will define your ability to stay operational and thrive tomorrow.
A Call to Action
As cyber threats grow more sophisticated, firms will want to act decisively to safeguard their operations. Conducting a baseline security assessment, aligning goals with IT teams and vendors, and investing in training and detection tools are essential steps. Business will also want to regularly update policies and ensure backup integrity to further strengthen defenses. For guidance, contact Antonia McAvoy, Partner on PBMares’ Cybersecurity & Risk Advisory team or Jennifer French, Partner on PBMares’ Construction & Real Estate team.
Watch: Webinar Recording | Cybersecurity in Construction & Real Estate: How to Mitigate Risks from Ransomware, Social Engineering, and Beyond






